Introduction
Let’s set the scene of this scenario…
You have a Windows estate running Windows 10 or 11 Pro. You have M365 licences in your tenant plan which includes Windows 10/11 Enterprise licences and you want to apply those Enterprise licences to your devices.
From with Windows 10 version 1703, a feature called ‘Subscription Activation’ was provided. This enabled users to ‘step-up’ from a Windows Pro licence to Windows Enterprise licence automatically, so long as the users is assigned a Windows Enterprise E3 or E5 licence option in their M365 tenant.
The Subscription Activation feature eliminates the need to manually deploy Windows Enterprise or Education images on each target device, and then later standing up on-prem key management services such as KMS or MAK based activation, entering GVLKs, and subsequently rebooting client devices.
It’s important to note that the Windows Enterprise subscription activation is designed to ‘step-up’ a device from Windows Pro to Windows Enterprise. Therefore, your device is required to have a Windows Pro license activated as a foundation. For most device procured for business, the Windows Pro key is built-in to the firmware of the device – but it’s worth noting if you’re testing in a lab environment where your device isn’t initially assigned a Windows Pro licence.
For Windows Enterprise Subscription Activation to function, there a several prerequisites which need to be in place. This blog is aimed at organisations which have Active Directory on premises and synchronise their AD objects to Entra ID (formerly Azure AD) via AAD Connect.
Prerequisites
The below provide a summary breakdown of the prerequisites required in the setup on AAD Connect:
- AAD Connect | Setup Check/Update
- AAD Connect | Entra Hybrid Join
- AAD Connect | Review/Amend OU Sync Scope
- Client Device | Internet Access to Entra ID via SYSTEM Account
- Client Device | Internet Access to Entra ID via User Account
- Client Device | SSO Local Intranet Settings
- Client Device | Windows Pro Licensed and Activated
- Entra ID | Valid Subscription Present
- Entra ID | Applicable Users Licensed with Windows Enterprise
AAD Connect | Setup Check/Update
To facilitate Windows 10 Enterprise Subscription Activation, AAD Connect needs to be configured with the following:
- Version of 1.1.819.0 or above (you need to be v2 now anyway)
- Entra Hybrid Join enabled and configured
- Sync scope to include the OU’s which contain the applicable computer objects
AAD Connect | Hybrid Azure AD Join
An Entra Hybrid Joined device is one that’s joined to Active Directory on premises and also sync and joined to Entra.
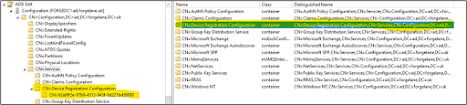
Configuring Entra Hybrid Join via AAD Connect essentially creates a Service Connection Point in Active Directory on premises with details on your M365 tenant.
That SCP will be used by a client device as part of the Entra Hybrid Join process when enabled via AAD Connect.
NOTE: Instead of configuring an SCP via AAD Connect, you can choose to control which devices attempt Entra Hybrid Join by using targeted deployment – This essentially lets you deploy two registry keys to the devices you wish to target for Hybrid Join. See the following for more details on that route – https://learn.microsoft.com/en-us/entra/identity/devices/hybrid-join-control .
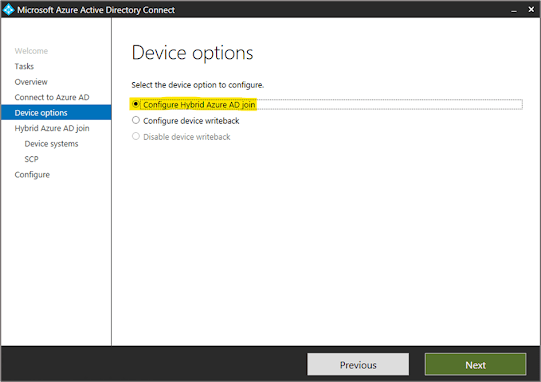
To deploy the SCP via AAD Connect. Within the AAD Connect wizard navigate to Configure Device Options:


Below is an example of the where the SCP shows in Active Directory:
AAD Connect | Review/Amend OU Sync Scope
For a device to become Hybrid Azure AD Joined, the sync scope of AAD Connect needs to include the organisational units which contain the user accounts which will have a Windows 10 Enterprise licenses assigned and computer objects which require a Windows 10 Enterprise Subscription to be assigned.
If required, amend the scope using the AAD Connect wizard as shown below:

Client Device
To allow user to carry out Windows 10 Enterprise Subscription Activation on a Windows device, the following needs to be configured on the client side:
- Internet Access to Azure AD via SYSTEM account
- Internet Access to Azure AD via User Account
- SSO IE Local Intranet Settings
- Device licensed and activated with Windows 10 Pro
Client Device | Internet Access to Azure AD via SYSTEM Account
Before a user can successfully obtain a Windows 10 Enterprise Subscription Activation, the device in question must be Hybrid Azure AD Joined.
For a device to become Hybrid Azure AD Joined, the built-in SYSTEM account requires internet access to Azure AD for the following addresses:
- https://enterpriseregistration.windows.net
- https://login.microsoftonline.com
- https://device.login.microsoftonline.com
- https://autologon.microsoftazuread-sso.com
- Your ADFS server address if you have one e.g. https://sts.company.com
There is a scheduled task in Windows 10 under \Microsoft\Windows\Workplace Join called Automatic-Device-Join. The task is scheduled to run as the SYSTEM user and run with the highest privileges. The task is triggered to run every time somebody logs onto the workstation and every hour for the duration of 1 day.
The main point of the scheduled task is to obtain a unique certificate which is then written to the UserCertificate attribute. Without the UserCertificate attribute populated, the computer object will not synchronise from AD on premises to Azure AD.
If your device has direct access to the internet this should function without an issue. If a proxy server is used to filter web traffic, this can cause issues where the SYSTEM account is unable to access Azure AD over the internet.
Where a proxy server is in place and you don’t have direct internet access via your default gateway, you typically have the following options:
1. Make network/proxy changes to allow traffic to Azure AD via the default gateway
2. Make exceptions and push out proxy settings for computer objects via SYSTEM account for example via WPAD (Web Proxy Auto-Discovery) – https://docs.microsoft.com/previous-versions/tn-archive/cc995261(v%3dtechnet.10)
Automatic Device Join Scheduled Task
Details on the scheduled task which obtains and writes the UserCertificate back to AD on premises are below:




userCertificate Attribute
In the example below you can see the userCertificate attribute is populated after the Automatic-Device-Join task has run:
Before:

After:

AAD Connect Device Sync Rule Filter
The below show the AAD Connect Sync rule which qualifies whether a computer object has the userCertificate attribute populated to qualify it for sync to Azure AD:



Test Azure AD Connection for SYSTEM account
To test the connectivity to the internet under the context of the SYSTEM account, you can download and run the Test Device Registration Connectivity Script from Microsoft. This creates a temporary scheduled task which runs as the SYSTEM account to test for successful connection to Azure AD.
https://gallery.technet.microsoft.com/scriptcenter/Test-Device-Registration-3dc944c0
Example where it fails:

Example where it’s successful:

Manually setting proxy for SYSTEM account
Below is an example of how to set the proxy server to be used under the context of the SYSTEM account. This is helpful for testing and troubleshooting:

Entra Hybrid Join status
Below is an example of a device showing as Hybrid Azure AD Joined in Azure AD:

Client Device | Internet Access to Entra ID via User Account
For a user to successfully obtain a Windows Enterprise Subscription Activation from an Entra Hybrid Joined machine, the user must have internet access. This can be via a proxy server or direct internet access via the default gateway of the machine.
Client Device | SSO IE Local Intranet Settings
In order to provide Seamless SSO for the license subscription to works silently, the following URL’s should be added into the users Local Intranet zone in Internet Explorer:
You must also enable Allow updates to status bar via script in the user’s Local Intranet Zone.
Push Out Settings via Group Policy
You can push out the Local Intranet Settings to users via a Group Policy. Below is an example of the settings which need to be configured under the user context:

Client Device | Windows Pro Licensed and Activated
For the step-up in license from Windows Pro to Enterprise to occur, you’re required to have your device licensed and activated with Windows Pro as a foundation.
Note, starting from Windows 10, version 1803 pulls activation keys directly from firmware where the device support firmware-embedded keys. It is no longer necessary to run a script to perform the activation step on Windows Pro prior to activating Enterprise.
Windows Edition Check
Below is an example of how the Windows 10 Pro license should display prior to step-up in license. Disregard the partial product key as this may be different prior to the step-up in licensing:





Azure AD
To allow a user to carry out the step-up in licensing from Windows Pro to Windows Enterprise the following needs to be in place in Entra ID:
- An applicable license plan in the M365 tenant
- A license assigned to the applicable users for the step-up in licensing
Azure AD | Valid Subscription Present
A valid subscription will need to be procured and showing as present in the Azure AD/Office 365. This typically shows under a Microsoft 365 E3 or Microsoft 365 E5 but can also show as a different license plan.
Azure AD | Applicable Users Licensed with Windows 10 Enterprise
The user account that will used to carry out the license step-up activation need to have a Windows Enterprise license.
An example from the Entra ID portal is below:

Enable Licence Subscription
The enabling licence subscription tasks can be found under scheduled tasks:





Windows Subscription Activation
With the previously outlined prerequisites in place, after a user has logged into the Windows Pro workstation, you should find the license has been updated to Windows Enterprise.
- Note, in some places the license will still appears as Windows Pro.
- Note, that the partial product key should show with the value 3V66T.
- Note, a user can license up to 5 devices with their user account. The activation is like a queue, the 1st activated device will drop off the list when a 6th one is activated etc.
- At the present time, there’s no documented way to verify which and how many devices have been licensed by user account in Entra ID.
- Upon revoking the license from the user in M365, the license will downgrade back to Windows 10 Pro.





